Merlin Lab Performance Fee Minting Incident Analysis
Fool me once, shame on you. Fool me twice, shame on me. Fool me three times, shame on both of us.

Disclosures: Merlin Lab has engaged WatchPug to perform the 4th audit on their updated security code.
The Exploit
On May 26, 2021, 03:59:05 AM +UTC, less than 48 hrs after the Autoshark hack. Merlin Lab, well, another Bunny fork, been attacked in a similar fashion to the Bunny and the Autoshark hack.
As a result, the hacker has taken out 240 ETH (680K USD).
How?
Pretty much the same as The Bunny Hack and The Autoshark Hack.
Check out the Transaction Details on BscScan.
- Added a small sum of deposit to the LINK-BNB Vault (with this transaction).
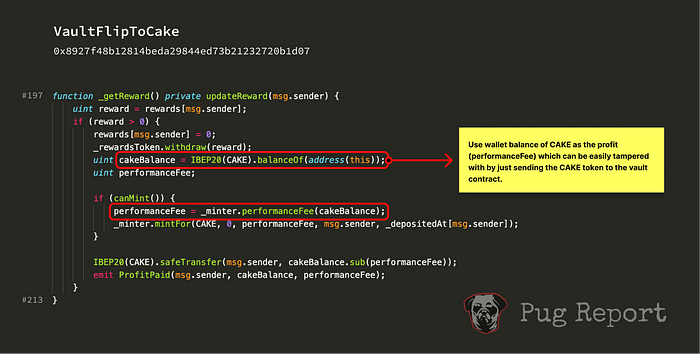
- Send 180 CAKE to the LINK-BNB Vault contract. (this is important! this is the key that leads to the hack.)
- Call getReward with the deposit of LINK-BNB Vault from the first step.
- With the rather large amount of CAKE token in the wallet balance of the vault contract (sent by the hacker at step 2), it returned a large amount of profit (see detailed analysis below). As a result, the system minted 100 MERLIN as a reward to the hacker.
- Repeated 36 times. Got 49K of MERLIN token in total.
- Swapped MERLIN token into 240 ETH and transferred out of BSC using Anyswap.
Why?
Again, pretty much the same as The Bunny Hack and The Autoshark Hack. Except for this time, it’s even simplier:
About Us
WatchPug is a smart contract security team with the goal of elevating the security, privacy, and usability of the current DeFi ecosystem. For the need for smart contract auditing, please contact us at Twitter or Telegram.
Donation: 0x227d72Ec9f332292523f64032DD25111676404aA
